Critical Bug in WordPress Plugin Opens 200,000 Sites to Hackers
February 18, 2020
Many of us know of and probably use WordPress and we all know about the ease of installing any plugin you like to add extra functionality to your website. However, WordPress also offer theme plugins to allow you to change the style of your website. A popular WordPress theme plugin with over 200,000 active installations contains a severe but easy-to-exploit software vulnerability that, if left unpatched, could let unauthenticated remote attackers compromise a wide range of websites and blogs.
The vulnerable plugin in question is 'ThemeGrill Demo Importer' that comes with free as well as premium themes sold by the software development company ThemeGrill.
ThemeGrill Demo Importer plugin has been designed to allow WordPress site admins to import demonstration content, widgets, and settings from ThemeGrill, making it easier for them to quickly customize the theme.
What could an attacker do?
When a ThemeGrill theme is installed and activated, the affected plugin executes some functions with administrative privileges without checking whether the user running the code is authenticated and is an admin.
The flaw could eventually allow unauthenticated remote attackers to wipe the entire database of targeted websites to its default state, after which they will also be automatically logged in as an administrator, allowing them to take complete control over the sites.
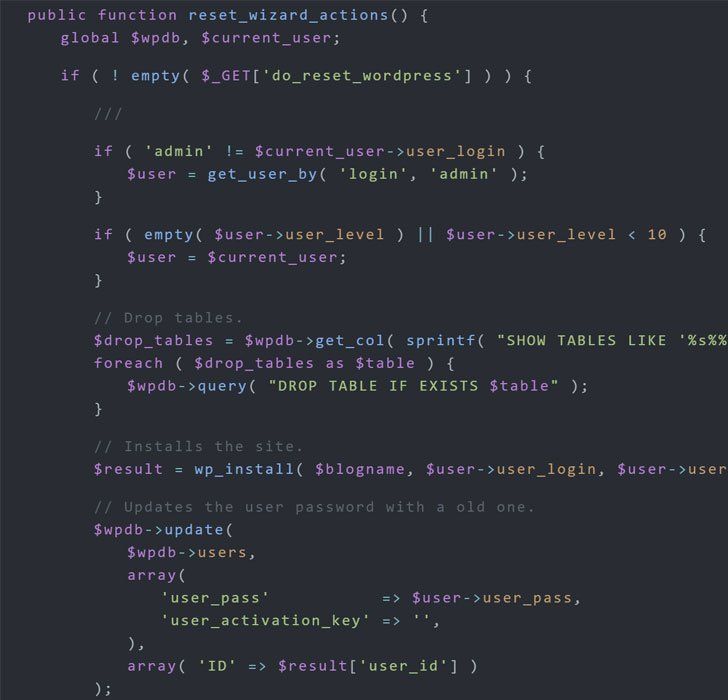
Here we see, in the screenshot above, that there is no authentication check, and only the do_reset_wordpress parameter needs to be present in the URL on any 'admin' based page of WordPress, including /wp-admin/admin-ajax.php.
This vulnerability affects ThemeGrill Demo Importer plugin version 1.3.4 up to 1.6.1, all released in the last 3 years.
This is a serious vulnerability and can cause a significant amount of damage. Since it requires no suspicious-looking payload, it is not expected for any firewall to block this by default, and a special rule needs to be created to block this vulnerability.
What happens now?
This vulnerability was responsibly reported to ThemeGrill developers, who then released a patched version 1.6.2 yesterday. Please check to see if this patch is available and install it as soon as possible.
The WordPress Dashboard automatically notifies administrators when a plugin needs to be updated, but we recommend that you choose to have plugin updates automatically installed instead of waiting for manual action.
Follow Us
Be the first to know
You might also like

DevOps is a popular practice, especially among large organizations. However, while it comes with numerous benefits, it presents numerous risks as well. One notable challenge is the increased velocity of deployment, which often complicates how developers implement and ensure application security throughout the development and deployment process. DevOps is a popular practice, especially among large organizations. However, while it comes with numerous benefits, it presents numerous risks as well. One notable challenge is the increased velocity of deployment, which often complicates how developers implement and ensure application security throughout the development and deployment process. According to a recent survey, almost 80% of CIOs expressed concerns about the difficulty of discerning trusted elements from untrusted ones within DevOps environments. In particular, the pressure to deliver services at a faster pace sometimes prompts DevOps teams to take security shortcuts, resulting in potentially costly repercussions. These include data breaches, application downtime, and compliance violations. So, how can you strike a balance between the demand for agile DevOps practices and the need to maintain robust security measures?

Testing applications for security flaws during production is a vital process of the development lifecycle, and this is where Dynamic Application Security Testing (DAST) comes in. DAST is a security testing approach in application security (AppSec), in which testers assess an application in real-time, while it’s actively running. This process can be conducted even without testers knowing the application’s internal interactions or system-level designs. Applications fuel the engine of the world’s economy, but enterprises can encounter substantial hurdles when striving to retain a competitive advantage in a rapidly changing digital landscape. Businesses must continuously pursue inventive solutions, even as they contend with sophisticated adversaries looking to exploit opportunities to disrupt operations, compromise vital information, and inflict harm. According to recent research, approximately 17% of cyberattacks aim to exploit vulnerable web applications. Yet, 98% of web applications are susceptible to attacks that can lead to malware infection or redirect users to malicious websites. All the while, 72% of these vulnerabilities result from coding errors. Testing applications for security flaws during production is a vital process of the development lifecycle, and this is where Dynamic Application Security Testing (DAST) comes in. DAST is a security testing approach in application security (AppSec), in which testers assess an application in real-time, while it’s actively running. This process can be conducted even without testers knowing the application’s internal interactions or system-level designs. This is because DAST tools operate without access to the application’s source code. Instead, they emulate genuine attacks, akin to those carried out by real hackers, to identify security weaknesses. This “black box” testing method examines the application from an external perspective, scrutinises its runtime behaviour, and observes how it reacts to simulated attacks. These simulations help evaluate whether the application exhibits vulnerabilities and if it is potentially susceptible to malicious attacks.

In this blog post we look back at the origin of the term “hacking”, as well as how activities that might be described as hacking have existed throughout history, even prior to the advent of computer systems – and what if anything these can teach us today. Hacking is attacking and breaking into computer systems illegally… isn’t it? The meaning of the term “hacking” has in fact changed substantially over time, morphing from describing essentially benign (or at worst mildly disruptive) activities into its modern attribution to largely criminal and illegal activities. What’s more, in its original usage, “hacking” doesn’t necessarily even need to involve computer systems at all. In this blog post we look back at the origin of the term “hacking”, as well as how activities that might be described as hacking have existed throughout history, even prior to the advent of computer systems – and what if anything these can teach us today.